Have you always wanted to create your own secret code? Whether you want a secret way to talk to your friends, or you’re just interested in creating your own, ciphers are a lot of fun to learn about and create for yourself.
A lot of computing’s early successes were in the field of codebreaking. During World War 2, the Allies had to find a way to crack the German cipher in order to understand what they were doing and where they were going.
A lot of mathematicians stood up to the task, including Alan Turing, who would go on to become a father of modern computing. Powerful computers such as the Bombe were built solely for the purpose of processing the code and trying to crack the fundamentals on which it was built.
So, how do you build a cipher, and what can you do with one? To start, let’s take a look at a very simple cipher you can create in a few minutes; a simple substitution code.
What is Simple Substitution?
A simple substitution code really lives up to its namesake! The entire code is built around substituting letters for other letters, and it’s very easy to create. It involves swapping letters in the alphabet around to create an unreadable sentence for anyone who doesn’t know the code. For everyone who does, however, they can easily translate the sentence and unlock its true meaning.
So, how do you make one? First, you begin by creating an alternate alphabet. This is done by creating a table two cells high and 26 cells wide. In the top row, write out the alphabet from A to Z. Then, in the bottom row, you ‘assign’ each letter of the alphabet with a different, unique letter. For example, if you write down A, B, C and D in the top row, you can then write S, E, Z, and R underneath each of those letters in the bottom row, like this:

Make sure none of the letters share a substitution (both A and G being assigned to S, for example) or else translating your code will get very confusing!
When you complete this from A-Z, you’ll have a normal alphabet above a scrambled one. This is your cipher! Easy, isn’t it? The idea now is that we spell words using our scrambled alphabet instead of the normal one (or else it won’t be much of a code!). We give everyone we want to read our secret messages the table we created. Then, when we write a message with the scrambled alphabet, people with the solution for it can match it back to the regular alphabet and decipher the code
For, for instance, let’s say we want to write the word BAD. Look back up at the table we created earlier. If you see, we have E assigned to B, S assigned to A, and R assigned to D. So, instead of writing BAD, we can instead use our cipher and write ESR by using the table. The sentence “a bad dad” through this cipher becomes the unreadable “s esr rsr”. The idea is that everyone else sees a ‘random’ jumble of letters, but you and everyone with your table knows better; it’s just a sentence written using a scrambled alphabet!
An Example
So, let’s give simple substitution a shot! Let’s say you and a friend want to meet in secret somewhere to discuss your plans. You don’t want to risk other people learning where you meet, so you decide to use a cipher to tell each other where to meet.
One day, your friend sends you the following cipher alphabet:
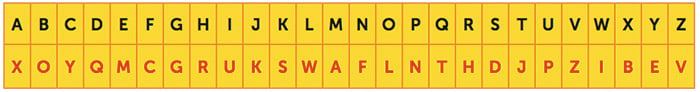
A little while later, he sends this message:
“wmj’d ammj fmxh jrm djlhm oe jrm nxhs!”
Can you work out what he’s trying to say?
Similarly, if you wanted to respond with this:
“Okay! Let’s meet there after school, don’t be late!”
How would you write it using the cipher?
Breaking the Code (Advanced)
Unfortunately, Simple Substitution isn’t a very strong cipher! This makes it inefficient for more high-tech codes, such as military and for vital documents. So, why isn’t it great? Because of its nature of replacing letters of our own alphabet, you can reverse-engineer the cipher by applying patterns of the English language to the problem.
If you see a letter on its own in a substitution cipher, there’s only really two solutions it could be: an A (“A cat is here”) or an I (“I saw a cat”). This then narrows down what the letter can be, and you can apply that knowledge to the rest of the cipher. For instance, if you see an X by itself, that X will be either an A or an I. Then if you see ‘xn’ in the sentence, it might be ‘an’, ‘if’, ‘is’, etc, which gives you for options for the letter n in the cipher.
If the person setting the cipher kept punctuation within their code, you’ll be able to deduce letters that way. If you had a cipher with “gtsg’p” in it, there’s a good chance the P might be an S (as in “that’s”), or a D (as in “that’d”)
Also, you can look for how often letters appear. If a specific letter ends up showing very little, you can probably deduce it’s one of the rarer letters in the alphabet, such as X or Z. More reoccuring letters might be one of the more well-used letters, such as vowels. Count the amount of times the letter appears and gauge what it might be depending on where it appears!
With this knowledge, can you crack the below sentence without a key at all?
“y ma rkjn usk’zz xjmxb m xswn zybn iqyr! yi’r iss iman, mow usk’jn mtzn is rnn yir njjsjr mow tnmi yi yd usk iju!”
When making your own cipher, how can you dodge these kinds of flaws? Perhaps you can remove the grammar entirely and write the code so people can still understand it without the need for apostrophes or commas. Maybe you can also tackle short word length by combining them together.
Answers
The friend’s message reads as follows:
“Let’s meet near the store by the park!”
In order to send “Okay! Let’s meet there after school, don’t be late!” using the cipher, you should send this:
“lsxe! wmj’d ammj jrmhm xcjmh dyrllw, qlf’j om wxjm!”
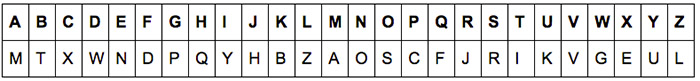
The solution for cracking the code without a key is this:
“I am sure you’ll crack a code like this! It’s too tame, and you’re able to see its errors and beat it if you try!”
It uses the following key:
External Links
Substitution Cipher Translation Tool: http://practicalcryptography.com/ciphers/simple-substitution-cipher/
More Kinds of Substitution Cipher: https://www.math.cornell.edu/~mec/2003-2004/cryptography/subs/substitution.html
Basic Solving Techniques: http://www.dummies.com/games/cryptograms/cryptography-101-basic-solving-techniques-for-substitution-ciphers/
Learn More
Wikipedia – Substitution Cipher
https://en.wikipedia.org/wiki/Substitution_cipher
Practical Cryptography – Simple Substitution Cipher
http://practicalcryptography.com/ciphers/simple-substitution-cipher/
Substitution Ciphers
https://www.math.cornell.edu/~mec/2003-2004/cryptography/subs/substitution.html
Simple Substitution Cipher Encoder
http://substitution.webmasters.sk/simple-substitution-cipher.php










